-
I wasn't sure whether to start a new thread or not
To my untrained eye, this looks extremely significant.
Overall summary- https://wikileaks.org/ciav7p1/
- one of many revelations
-
OK, I was bored and started reading it.
NEWSFLASH! Intelligence agency develops tools to gather intelligence! OMG!
NEWSFLASH! People working for intelligence agencies work from embassies using cover titles, travel on Diplomatic passports and don't tell immigration officers exactly what their job is! OMG!
Oh well, I found it funny anyway.
-
The important bit, coming out with this timing, was the detailing of how the CIA (apparently) have a tool that lets them hack with the footprint of other foreign agencies. EG the Russians.
That's why this 100% belongs in
bullshit spamconspiracy theories.It came out in the midst of a Russia meltdown & gives cover to the idea that anything "on" anyone in the whitehouse had zero to do with the Russians & was planted by the CIA. And that the CIA hacked the DNC and made it look like the Russians. And anything that smells of Russians now is actually the CIA using this tool.
OR
It's Wkileaks leaking to help the WH just as they did during the election, at the behest of the Russians & with full collusion between Assange & Bannon.
Take your pick, both are equally bullshit.
-
a point not mentioned below is that by last year, the CIA's CCI (Centre for Cyber Intelligence) more than rivals the NSA, has minimal accountability, and 5000 registered hackers/users.
This is a list (which I am posting here from another site, I didn't make it) of the main wikileaks points:
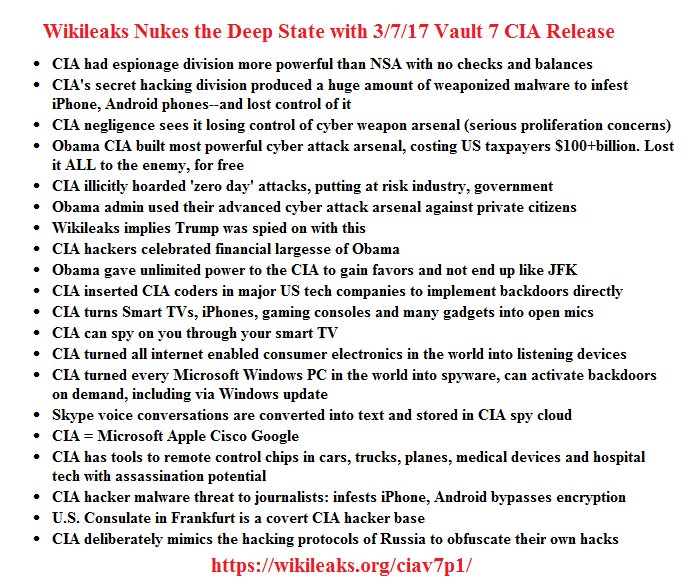
....goes to unplug his 55 inch Samsung smart TV.....

-
I was pretty amused by this:
mrpippy 1 hour ago [-] Also: OmniGraffle and Sublime Text license keys (registered to "Affinity Computer Technology") https://wikileaks.org/ciav7p1/cms/page_25264141.html https://wikileaks.org/ciav7p1/cms/page_9535650.html replymo17i 1 hour ago [-] I tried Sublime Text license key and it worked! reply -
@gollum said in Wikileaks CIA releases.......:
When do they start releases hacks that make the Russians look bad? Oh.. yeah..
I am amazed how many people think a Russian proxy tossing information out is awesome.
Its bizarre that people think this weirdos behaviour is somehow constructive and most of the time his "revelations " are a let down or obvious to most people anyway. And like you said its completely one way, if he's as awesome as he thinks he is when it comes to hacking surely he can get past Russias cyber security? It seems more likely they've been drip feeding him stuff for years knowing that the narcissistic douche would happily take credit for it.
Since the election there's been a weird change in attitudes to Assange and wikileaks , he was a hero to leftards but now rwnjs like Sarah Palin are saying this about him.
Also he might be banging Pamela Anderson.
-
Its not since the election.
He leaks against the US - as everything he is given comes via the Russians, so whoever is in power hates him, when he leaked attrocities in Iraq the left loved them because it confirmed their ideas & the right hated him, when he leaked against Hillary the left hated him because it helped the GOP & the right came out & praised him, when he leaks against Trump... well, thats never happened so we don't know. But I'm going to guess the right will hate him. Even now the establishment right (McCain etc) fucking hate him with a vengence. Tho' to be fair they've consistently hated him right through.
-
Did you understand or find this useful -
Omnigraffle License Keys
FBBS-VPBC-BKZK-ACIN-DQHB-NDX (User #?) IEGR-ORUJ-BDVV-CSIN-DQHB-NDX (User #77146) HEOI-YOEE-JYYT-FFIN-DQHB-NDX (v5) (User #77147.) LAEM-IDBD-GWAO-HFIN-DQHB-NDX (v5) (User #15728648.(User #71317) ) HUXL-TPCG-HWMS-IKHQ-OUJJ-GEL (v5) (User #77148.)?
If not, the other 99% is not going to be that popcorn friendly. There were thousands of files leaked during the election & the one with most traction was interpreted (wrongly) that a pizza restaurant was a peedo site. Almost everything leaked will not be remotely understood by anyone & in trying to they'll get it wrong or rely on idiots to interpret it for them (who get it wrong). The odd software key is actually the only stuff that most people will find useful, and 99% of people will try & use it to activate MS Word.
-
@Frank if the first 1% can be thought of as a trailer to promote the full release then it will be up for a Razzie.
What has been released is designed to grab headlines and excite the public. It is nothing new and is not exclusive to the CIA (as is being made out)
None of this is 'Eye in the Sky' security fantasies or tinfoil hat material. It is commonsense security stuff.
I don't see how it's big news about the Samsung TVs. Basically just work on the premise that anyone that wants to access anything electronic can do so whether it is a games console, a webcam, a smart tv, a cable strung from your house to a junction etc etc.
There's a reason why sensitive information is handled only on secure systems electronically and physically it is handled within secure environments and skifs.
Want to know where classified material is handled? Look for the metallic mesh curtains, to stop anything electronic being accessed simply from long range.
It's a known game. It is as funny as hell in areas like Canberra where embassies are grouped together within line of sight. You can sit in the tea room of the NZ High Comm and talk shit in full knowledge that the Chinese across the road probably have a listening device tuned right at you from across the road. The Aussies even have a spurious DFAT 'training centre' on the hill above the Chinese (and PNG/Canada/NZ/UK)I think it's hilarious how many people think these releases are shocking as they are probably reading all about them on a Huawei device.
-
A lot of whats front page news on this came out at least 2 or 3 years ago. EG your TV might listern to you, CNET flagged that over 2 years ago (link)
and - even better, its in the fricking Samsung agreement you get with your TV -
"Please be aware that if your spoken words include personal or other sensitive information, that information will be among the data captured and transmitted to a third party through your use of Voice Recognition."
The Guardian highlighted in 4 years ago -
It (LG) conceded that the system also collected filenames of attached USB disks, which it said was "part of a new feature being readied to search for data from the internet (metadata) relating to the program being watched".
-
@gollum
seems different:your link detailed information leaking out of the software feature Voice Recognition, which can be turned on and off...
Please be aware that if your spoken words include personal or other sensitive information, that information will be among the data captured and transmitted to a third party through your use of Voice Recognition."and here is the CIA hacking malware:
Weeping Angel runs just like a normal TV app, not unlike YouTube, but in the background, capturing audio but not video. It can, however, also recover the Wi-Fi keys the TV uses to later hack the target's Wi-Fi network, and access any usernames and passwords stored on the TV browser, explained Matthew Hickey, a security researcher and co-founder of Hacker House, a project to encourage youngsters to get into cybersecurity. There was also a feature dubbed "Fake Off" where the TV would continue recording even when shut down.Hickey, who reviewed the CIA notes on the project, said it appeared the malware would infiltrate the TV via a USB key, as the notes on Wikileaks indicated USB install methods were disabled in a specific firmware. He said, however, that there's still a chance the CIA has remote infection techniques.
He noted that the attacks would likely be limited, in that the CIA would have to be nearby to harvest the stolen data. "Effectively they install an application onto your TV through USB, they go away on their spying business and come back with a Wi-Fi hotspot later on. When the TV sees the CIA Wi-Fi, it uploads all of the captured audio it has recorded of people around the TV, even when they thought it was off."
Wikileaks CIA releases.......



 Here's How The CIA Allegedly Hacked Samsung Smart TVs -- And How To Protect Yourself
Here's How The CIA Allegedly Hacked Samsung Smart TVs -- And How To Protect Yourself
